Welcome to the new year of AV MSP newsletters! In addition to regularly writing about audio visual managed services, we are launching a monthly roundtable meeting to share ideas and solutions to AV service issues. Our first session is on January 30th at 12PM EDT. Sign up here to get an invite in and be notified of future events. We promise not to use your email for anything but letting you know about future roundtables.
The Main Story
Some time ago we wrote about the case for audio visual devices being classified as IoT devices. You can read that post here. The argument won’t be rehashed here – audio visual hardware is IoT and needs to be treated with care regarding security standards.
IoT devices are seeing an increase in malware attacks, being used in DDOS attacks, and posing more of a threat than ever before (source). Additionally, IoT devices are becoming a popular target for companies like the Toka Group, who provide infiltration services for governments. In all, IoT devices represent a large attack surface for hackers and should be treated with caution. Nobody wants to be the manufacturer or integrator who opened the gates to a cyber incident.
Thankfully, we have some guidelines on how we can ensure some security around such devices. The National Institute of Standards and Technology (NIST) is a US government agency that publishes standards and guidelines for all sorts of things from weights to time (they run the atomic clock in Denver, for instance). They have been publishing cybersecurity frameworks since 2014 and continue to revise those standards. They also have an IoT specific set of standards found here that provide information around implementing devices in an organization, guidelines for consumers, and standards for manufacturers.
NIST sums up IoT security with: “Many IoT devices cannot be accessed, managed, or monitored in the same ways conventional IT devices can. This can necessitate doing tasks manually for large numbers of IoT devices, expanding staff knowledge and tools to include a much wider variety of IoT device software, and addressing risks with manufacturers and other third parties having remote access or control over IoT devices.”
Remember that just because a device can be connected to a network doesn’t mean it needs to be. NIST.IR.8228, found here raises some important questions regarding deployment of IoT devices:
- What data does the device collect?
- Does it indiscriminately collect data?
- Does data collected need protecting?
- What privacy concerns rise when you implement devices like cameras for occupancy and attendance?
Adding to those a few of our own queries:
- Does the device require internet connectivity?
- What damage or risks does someone having remote access to the device pose?
- What risks does the software or cloud service for managing the IoT devices pose?
- What are you going to use the data collected for?
- Do you have the staff to appropriately manage the number of IoT devices you are deploying?
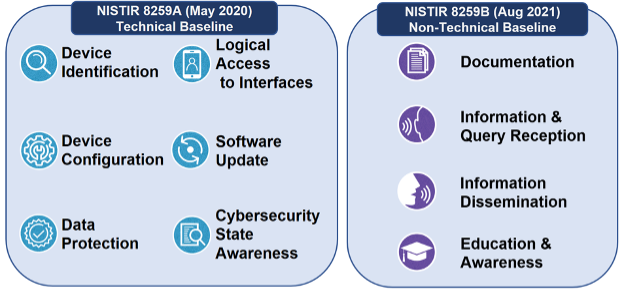
While the IoT deployment guide (SP 800-213 Series) is worth a read, we’re going to focus on the manufacturers of products. As you look at the AV landscape through the lens of IoT security, you’ll quickly see that some manufacturers are not security conscious and will put you at risk. Based on the NISTIR 8259 Series, specifically the NISTIR 8259a document (https://csrc.nist.gov/pubs/ir/8259/a/final), we’ve made a quick checklist for evaluating IoT devices. Pages 5 through 10 have the details of why these are important; we recommend reading the chart. While this is a simple checklist, it works into a bigger topic of risk management and third party risk assessments, something you should have ready for evaluating hardware, software, and vendors.
Here we go:
- Can the IoT device be uniquely identified? This means that there must be unique MAC addresses, serial numbers or other device-specific identifiers that can be located by authorized users.
- Can the IoT device’s configuration be changed and limited to authorized users? This also includes restoring a secure configuration in case of error or other device issues.
- Does the IoT device protect the data it stores and transmits? This means that the data should not be transmitted unencrypted or be accessible on the device without authorized access. NIST recommends that you should also be able to configure the cryptography used.
- Can the IoT device restrict access to its local and network interfaces? This could mean restricting access based on user roles or credentials and should also limit the ability to access the device should its state change, like a factory reset.
- Can the IoT device’s software be updated only by authorized users, using a secure, configurable method? Software updates should be able to be done via remote or local means, verified before they are installed, and can roll back the installation to a previous version.
- Can the IoT device report on its cybersecurity state? The device should be able to tell whether it is in the correct state, report the state to another service (like sending a log to a server), and prevent anyone unauthorized from altering the state.
Numbers 5 and 6 are where most devices will be challenged. Firmware rollouts in AV gear are notorious for being difficult to perform and hard to reverse. Similarly, they are not reporting on any security states; in some cases that is a manual check, or just not something the device is capable of.
There is another document, NISTIR 8259b, that outlines some non-technical standards for IoT, but we’ll cover that another time around running a cyber security program.
We hope this gives you some food for thought around IoT devices and some of the inherent risks. If you’d like to keep up with IoT security, here is a decent link: https://www.schneier.com/tag/internet-of-things/
An Asset Management Note
An addendum to the asset management newsletter – an additional resource: https://theiam.org/knowledge-library/asset-management-an-anatomy. This is by the Institute of Asset Management and gives some high-level information about the how and why of asset management. This is particularly useful if you’re looking for funding for an asset initiative.
Related to assets, figuring out the skills on your teams is also a useful way to understand where your organization sits in its available capabilities. Take time to interview team members, find out about experience, certifications, and plan on training to fill gaps. For a simple survey of skills, you can put together a list of soft skills, certifications, and technical skills; rate each team member on where they stand (1 to 5 rating scale works just fine); and then see where you have gaps in your team and gaps at an individual level.
News and Links
Yorktel has been purchased by One Equity Partners. While this may help them with growth, acquisition by an equity firm always comes with its own downsides. https://www.yorktel.com/press-releases/yorktel-announces-acquisition-by-private-equity-firm-one-equity-partners/
CES 2025 just wrapped up and we saw a lot of oddball devices (like an AI spice dispenser), but in our world, we’re seeing the evolution of TVs happen. Sadly, there is still a heavy focus on AI, whatever that will do. Ars Technica has a nice op-ed on the state of TVs at CES https://arstechnica.com/gadgets/2025/01/ces-2025-teases-alarming-smart-tv-future-loaded-with-unwanted-software-gimmicks/
AVIXA reports a slowdown in commercial/pro AV expansion. Everything looks flat in 2024 and there aren’t many good signs for an uptick in 2025. https://www.avnetwork.com/news/avixa-report-a-slowdown-in-pro-av-expansion
The Marketing
Thanks for reading, here’s an advert! We are AV MSP. We provide audio visual managed services directly to corporations, universities, and other organizations with large AV environments. We also provide services in collaboration with AV integrators and IT MSPs. All of this is done with modern ITSM software and standards. If you’re looking to elevate your services in the new year, please reach out to us at sales@av-msp.com to chat. You can also follow us on LinkedIn at https://www.linkedin.com/company/av-msp/, on Bluesky at https://bsky.app/profile/av-msp.com, and of course on our website at https://av-msp.com.
Like this newsletter and want to get them delivered to your mailbox whenever we bother to write one? Sign up below.